This is an old revision of the document!
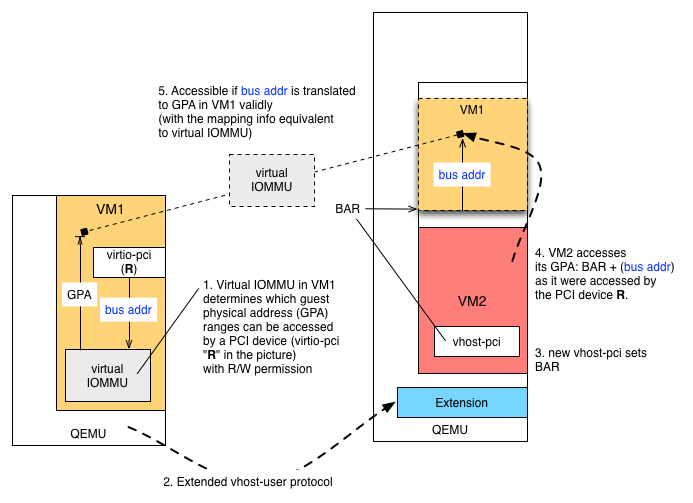
The following is my understanding and interpretation of the proposal from Michael S. Tsirkin. https://lists.gnu.org/archive/html/qemu-devel/2015-08/msg03993.html
Jun Nakajima
VM1, VM2 corresponding to the examples in his proposal. Basically VM1 can express access permission (R/W) to its guest physical address (GPA) space by virtual IOMMU. Typically, IOMMU (e.g. AMD-Vi and Intel VT-d) uses page tables that convert bus (I/O) address to GPA for a given PCI device to protect the rest of the system from the DMA operations. See https://www.kernel.org/doc/Documentation/vfio.txt for the details and VFIO. If you think about an imaginary (i.e. virtual) PCI device "R", you can set up mapping from bus (I/O) address to GPA for that device (because you can set up such mapping for each PCI device). This way, VM1 "gets full control of its security, from mapping all memory (like with current vhost-user) to only mapping buffers used for networking (like ivshmem) to transient mappings for the duration of data transfer only."